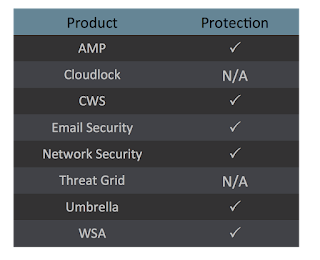
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between March 15 and March 22. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
For each threat described below, this blog post only lists 25 of the associated file hashes. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
Registry Keys
ThreatGrid
Umbrella
Registry Keys
ThreatGrid
Registry Keys
ThreatGrid
Umbrella
Registry Keys
Umbrella
Malware
Registry Keys
ThreatGrid
Registry Keys
ThreatGrid
Umbrella
Registry Keys
ThreatGrid
Registry Keys
ThreatGrid
Umbrella
Registry Keys
ThreatGrid
Umbrella
Malware
Registry Keys
ThreatGrid
![]()
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
For each threat described below, this blog post only lists 25 of the associated file hashes. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
- Win.Ransomware.Gandcrab-6900355-0
Ransomware
GandCrab is ransomware that encrypts documents, photos, databases and other important files using the file extension ".GDCB", ".CRAB" or ".KRAB". GandCrab is spread through both traditional spam campaigns, as well as multiple exploit kits, including Rig and GrandSoft.
- Win.Trojan.Remcos-6898089-0
Trojan
Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, and capture screenshots. Remcos is commonly delivered through Microsoft Office Documents with macros, sent as attachments on malicious emails.
- Win.Malware.Autoit-6897734-0
Malware
Autoit is a malware family leveraging the well-known AutoIT automation tool, widely used by system administrators. AutoIT exposes a rich scripting language that allows to write fully functional malicious software. This family will install itself on the system and contact a C2 server to receive additional instructions.
- Win.Ransomware.Cerber-6896901-0
Ransomware
Cerber is ransomware that encrypts documents, photos, databases and other important files using the file extension ".cerber."
- Win.Malware.Zbot-6896522-0
Malware
Zbot, also known as Zeus, is trojan that steals information such as banking credentials using a variety of methods, including key-logging and form-grabbing.
- Win.Malware.Ursnif-6896385-0
Malware
Ursnif is used to steal sensitive information from an infected host and can also act as a malware downloader. It is commonly spread through malicious emails or exploit kits.
- Win.Packed.Kovter-6895460-0
Packed
Kovter is known for its fileless persistence mechanism. This family of malware creates several malicious registry entries that store its malicious code. Kovter is capable of reinfecting a system even if the file system has been cleaned of the infection. Kovter has been used in the past to spread ransomware and click-fraud malware.
- Win.Malware.Upatre-6894504-0
Malware
Upatre is a trojan that is often delivered through spam emails with malicious attachments or links. It is known to be a downloader and installer for other malware.
- Doc.Downloader.Emotet-6894115-0
Downloader
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails.
- Win.Trojan.NetWire-6893426-1
Trojan
NetWire is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, remote desktop, and read data from connected USB devices. NetWire is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails.
Threats
Win.Ransomware.Gandcrab-6900355-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
- Value Name: xbnykvblxlz
- N/A
- 66[.]171[.]248[.]178
- carder[.]bit
- ransomware[.]bit
- ns2[.]wowservers[.]ru
- %AppData%\Microsoft\jfwwxp.exe
- 19b5f589a31dd4b6fd6fcda9e529f04adee6628740cfb4354b7fde94ca4c8fe8
- 2870e29273fac8161c571505e2081afe0aa8c9e198150923f9efcb15a0379e66
- 31bbc9f6a7d5b5c248c6379afcf7c7026fb0f3b521016d918edba1fad085a9cc
- 3e9ae9bb1061f2335cbca35ddfe71f7b93d8ff14a79c362b7a5e22a3c19f5af0
- 3f18aeab0f40e3f957807fdb6142cafcfd4faeac39b0f31df9e869cca981cb70
- 5a6f4af9f4c0230111b39ff7cf127db182738ed735fa72183f935f272491b53d
- 635cd9d2065acf51745629ff92e41c8b331d25376868cfde5ec3dfab91cd0026
- 961b6caacf88d67139309a5dbec806301a1e7fc8eec7db166d9d0d0120346cad
- a8d145d01780227cecb322d69d173248c122c5c5b5ffe74c28e1ef89958b4dd7
- c4e78e775a53a51eefc2b5dd4ce161bd1794119a02481e03b9917aba5279d9c0
- cfb324eb0b95048aa3248b4475902e575da996b63ff86cf78211424ec8c1c561
- e43d30708069f2ec0b0237144b23e2d337521174530caefd04728fcc0cbbfd6e
- fcefe7d20db180411dd0f1ae2749e622738d9b8e6cca09a01b870551823ccbd3
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Win.Trojan.Remcos-6898089-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: internat.exe
- <HKCU>\SOFTWARE\IYFIZFIFK-HKLTVU
- Value Name: exepath
- <HKCU>\SOFTWARE\IYFIZFIFK-HKLTVU
- Value Name: licence
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: Wordpads
- Remcos_Mutex_Inj
- iyfizfifk-HKLTVU
- 194[.]5[.]98[.]147
- 103[.]200[.]5[.]128
- N/A
- %LocalAppData%\Temp\install.vbs
- %TEMP%\pyrogenetic.exe
- %TEMP%\pyrogenetic.vbs
- %ProgramFiles%\Wordpads\Wordpads.exe
- 0a1d151c7170baace5e771feb217ee3a685f8af2ddf5c51571d321b2253fa48a
- 2b6ea3f861899440039f30018f2593a3202b27e3a7f7adec5d5a3703dce3ed59
- 2c125850f874973b605b04f2ca76d4ae3476bd495890a55f1be3d74de4ca5015
- 2ea12c4cf9c0c9a3926e0f77333a5e74faf1f4956ab4a599bfd1be6410a4a348
- 34ce4dbec1155384abd4eab34fa0bc7ca1ead6ae2c4be9a54299e051100245fa
- 55f209afba93e7a881ad14761b1349349548843a388af32e084a58fe51bc1d34
- 616ece9b51f1fead02cbc893af7f76240a84a39a9096b4d6cdb066b6ad8a7f4d
- 786fd0f58b0731ae1326c434ff77bb3f40405dc0fd9f2814d8b41265325920de
- b76d7be62eb4b198c540220e8b697e01fa80e42465ba314992002175b6593bae
- bdeea19cc4255537c110faa58fb74721e6503d8815cc62b0fe14a77eba0c4bef
- c4d675f3f5941b6488fc4c3ecf540c106ef21aa8b8be858cd9ed750888947032
- c5d8569dbe75f1725774befcd82f1f0cabd8baf07759d60f9b2691870954408f
- d414046e1fa2ab58f5cb5ea84db538bec4ccff435a7d7c2aab826ebfd584a518
- dcedf388c083bb55821749ed00e80c96e2aef01fe0e1a26bfdba8b9b8b3d1556
- e6d04db2794d86b03d8deb2d8c902f76dda946240dc8fbc82d7509c722fa571a
- e8649923e071a79f7810eddb32257d5782e39428da217cd5aa34af4c821cb0f6
- fa73eb7829ef969e79d43f647136bdcac25a9b3739961b0653e7bab640966f12
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Malware.Autoit-6897734-0
Indicators of Compromise
Registry Keys
- N/A
- altspace
- N/A
- charlesprofile[.]website
- %UserProfile%\archiveint\adalsql.exe
- %System32%\Tasks\Gfxv4_0
- 0df27d70990f8b8ec8b3df25cf1eb9666bf92526095da227080a0372c60aa588
- 287d43060fcca28466206776b5a147e83d3fd7de4230f1cd909953daa12d0156
- 43e9ecb0c189695bbb533ec47746edf76778aa1a8b0266f5ac267f79f5cef03d
- 4634ecfa0699f7408c84fc3c2cdb42601d372777237eec1fe0a58868ef693c1a
- 5721c80fb52b4db900819b1738db0ad82c502eb7d79e152edb9f2e371f3c9664
- 6635eb7fc5c7c454b6c5c19018820e249318c34305420cf27392c171df491635
- 6b327d6a88a18c1167637a8878bf441cfcf567e9c1e19a95c27b93c16e69b45e
- 7642637e654417d9add1a62ac596cb8d1d84f793749e9e4cc92a117e33d56133
- 87d5cafaf2e1bb5f56caa5aebd24fbf9941db0e079ba854fb9aaf3bce4c819b2
- 93cfe8d255a490ac9f173ceb7618a019a25b9246b87e0493acaa20dda799950c
- d8c4ea9786f6ddc62da7b3555b3efb138ca0c4a0348be83ecec060618db2c276
- e4503c499e82fa0bce07fd10fdcf132d4a0933d309973b94823366d97a05c4e6
- e48da123e2e08dd9f62abb56e630b8edfe4ea7977149bda53522bebacfb10d00
- f51011fa1fbfdf0be75a9300931d33b850b601a01d1a4bfab33c346e3fdde5f2
- f5bbc3ec89ae91eb6a25cbdb66c4a95b1756298815a50a9e0ce2f27ba57a878f
- f95c285f6632fecd805fab3e79d018ab4e34e2c230adac317a94ca55b15fd35b
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Win.Ransomware.Cerber-6896901-0
Indicators of Compromise
Registry Keys
- <HKCU>\CONTROL PANEL\DESKTOP
- Value Name: SCRNSAVE.EXE
- shell.{381828AA-8B28-3374-1B67-35680555C5EF}
- N/A
- cerberhhyed5frqa[.]vmfu48[.]win
- %SystemDrive%\Documents and Settings\All Users\# DECRYPT MY FILES #.html
- %SystemDrive%\Documents and Settings\All Users\# DECRYPT MY FILES #.txt
- %SystemDrive%\Documents and Settings\All Users\# DECRYPT MY FILES #.url
- %SystemDrive%\Documents and Settings\All Users\# DECRYPT MY FILES #.vbs
- %AppData%\Microsoft\Internet Explorer\apXmmhm1Ka.cerber (copy)
- %AllUsersProfile%\Microsoft\Dr Watson\tMYvM36CEP.cerber (copy)
- 001b33940ee8465748b743f0df809eae3a2a08a78af15243312584cce53393c1
- 01906006204a9a84fd0dd7d061aacbb093d09a8192c65cc55e3be6edd164c908
- 02f66c7648b064b49da5218664d1f5abbe954c6a02f46db9dac77358a0d9b92f
- 0830faf3346becd79a49df77f0d181c66bed86d1771622f0b8315e288ba29e77
- 0affee8e0b6dce3ec8c453b6a7ac92648bea9006a63c77b7efd36537adabf5b4
- 0d899afe8df44ba83ee7b02f621100ed721dd0bd9411d6d0a6e3935baa65cc0f
- 0df1130e9f23b007643dd0ed3375528cb08d0496b195401078fbd27d2fa5de10
- 0f3c4c70da6c8a58c0f6844eabc40773e0622f8a1e3f13370538112634ae0079
- 127d0879d93ff4fb65ff40d723480e62e0144483f4be7da0a739ceae9c446d3f
- 133a9faa5bd0bd157660e67bf208cdea7cde346836df7ed3f0619edf9e652313
- 1ab65651d3c70301f55f31fa294e215b1c72e9aa7f87d894e493b5e25d2d35d2
- 1ad4afdcb9a62b69473149a0e70c38822be0f566b6759922f730c074bffcd09c
- 1cd3e3a997e017a9ad7883dbee9ba8c71f416e56e1113c96d13290dd998ad8da
- 1df2e8bb31a42361b916a71aa2e816dcc7279b93a80b2613d5dd8681f007cec1
- 20e0fc147c170e25c8ba1dbb4e6d0dcafa6771659ba101b67e5b2176d41fb81e
- 2232654770e8440f3d4629753cc78bcc97b054c5df003ac3908da5b20d058659
- 2b5295639ab89940a16a9b7dc80f7eefbe065fd0bcbdb7d1c783cebd93dd9db8
- 2dae95760c360eadeba55f370e3e78e9761f436539ffc3cc1e8e91395722ab4b
- 2e87382ab956e8db123f80f8ecffeb61c4461b5c77d6deed2952c68b9a96f3d8
- 2ffc4d2116734e50078268c07b7b972d9d127e9d83513d331d13788c7c941990
- 31235847a5b061a60d79ad9f634455bfc95ce68667ec4df1fc479d147c794649
- 320281163724c2d356f3ba9e7ccab33fa06b584f841dcbed783cb65432f1498c
- 3374ca6683d9bb5434fa192eebe615ba6a609cbd8063c47eca42c47bb480e886
- 3444fa109868538f1b25a0b4e1e8b1b8545ae88e0dc4a71161e64a868826d301
- 369dc38935f947829cfa4c85e8262a594ef9bd1ece3479c980d90e62ebfeea68
Coverage
Screenshots of Detection
AMPUmbrella
Malware
Win.Malware.Zbot-6896522-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
- Value Name: AppInit_DLLs
- N/A
- 216[.]218[.]206[.]69
- N/A
- %SystemDrive%\PROGRA~3\Mozilla\thfirxd.exe
- %System32%\Tasks\aybbmte
- %SystemDrive%\PROGRA~3\Mozilla\lygbwac.dll
- 00ffecb86e72d9357a6bbd15b6354fc9213033f748d9b51b597fcc365a9e1f7d
- 010d598fc0465864690982eec5f30ef48c713916ef4e45a8d8d49420342df428
- 018edfb60377a0c076e1297bb407cd42b16ffb2c08d4d2aa32b860b061ca5ed3
- 01bce31e9de13c804a18643616bc34f64bd1c5b25bf8a10f422e2ad19fb7730c
- 02701dff6c0a0f71b66c9cf69bd895129e810a1a13bcb18be9a8388ff7821b89
- 02b10171ce53f9592cb441792f91f1d2a7ea1af92e8a814e3bbc42b647afff2c
- 02c63a651be113f6b1816a357a97af54141e2bd6d9ce4aa2827a629031b8eaf7
- 02e7cf905bba1542c36e54c120d57c583f6bf33fc15a4fea4e8a41187801b041
- 0491fc85d831a1f252b61ad87941db7174c53c1b849bc3fa67604251bdbc7fe0
- 060b3e97fe90a1c725a41fb0ffd3a01ff7b34c74f1460b68dcf05b668dd5521c
- 06b7d5b411bc5c2b50aa6a257b0799dfa4e098a249602c39a3a43160539087e3
- 06dea51ea8ec0bbe9578024339ef207c8cac340ca608b519c22999e109514b47
- 082549d3ad41312e5014c2ada5b99d6dfabc29f09b19ef4d1d9a7ec1297e8356
- 08807c13e43fd5d202c97c68e25c6178445a65cb0c8f957ff3dc17a293b11020
- 08d6916f9a64fc2e725d578d1c11c1f77894edc35373d7d308e039bc85e889a7
- 0997d72a90fbb50cc4fd395c6d9b5bc38f622f5bd66befc055fad32c19ae686e
- 0a5e7372e854b6ab82834abfaef00be3a1713ae3c921f3d693112482b8d91dff
- 0aa62de7c50e0d0498ff66687e0ed5ce905f7fe5014b765586ca64c283c2b595
- 0bca5fd01e55d40ca9d324e0011f56de76cab17d399f6655019f85cbe16ae060
- 0c3fea106ea5b2d0f943580279e0ddc729e210716ba82344a619ab901438511e
- 0d08edbe5a8d68b1a6c29fd0956514036a94638e6443db85c37c8e532d15a2c4
- 0d9c6fe9e4172a80ad9c912eebeecf2baa094012552267ad70d49d6f583add8f
- 0e9189428c742936b52149e2579844257ab381570b9c13d440fb3304b7cfd935
- 0ee3a3afec6551c3cdc20836f7d3ae8ac1b20cd7dfa6a14e379ca975d9b342b5
- 0f18e6faa5e6bc9e81e5cb5c51a7cbd03589eedae7565d1b270fdb803c78c437
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Malware.Ursnif-6896385-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- 91[.]134[.]203[.]113
- kkariannekatrina[.]company
- f61leeii[.]com
- qmitchelkp[.]com
- %LocalAppData%\Temp\~DFDEB0FC636A1346E9.TMP
- %LocalAppData%\Temp\~DFCE77235CFE7E5202.TMP
- %LocalAppData%\Temp\~DFD0DDA0AA1947567A.TMP
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\~DFA0E5.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\~DFBF00.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\~DFD9FC.tmp
- 002c189b365fecdd1a985d49bb4fb006c15efc47b1000defbdd6f4af1c11a19a
- 02a860f30efb515b8c290d7eec3aaacc31e13db934b950c12c46c2b418f44c6f
- 0698973ada3bb251a5d7d24af6532bfe757f26e21c5ccb4683ea90fa22000d31
- 0bf3ad196d5c033b96508b82a4627371b410a4171a112fe87749ffa35148e700
- 4e8a9df93d31b02390be3f76e8092bb8dd1296da7b583f0ef7d1e0a4b621f5c9
- 50e11389b6a65a77dd2806b0101c00c3ecab05c885904d8ed93fd7d5a22caa29
- 65365868838db8f45660946e8cf4e48420fef2f191087adff2c8525e1e9b92ab
- 68ac70dcad46e80bb89338cc239d9c7942a4d7baeb39c783cf7f3f41338afee6
- 72ea94949e5a93a9470f528c2e19fee632f1c35e6592e7466d230fcd4425adca
- 8b07ef958d6f3f94cb45580d4aaa99202870f35e6c309d94894c5601c861cfff
- 8ee22466de53f493c666b1f805bfad58f4b9d33b657e266dd65724efb96002e7
- 9124364a4c9db508a438403d4742db5ba39542753f2a67e4b1f77854962ca1d2
- ae0f77690e47a8662efaa1507002e3924c2d0986e6c1cd39d3d775e53ad982d2
- af421716811ae86cf1b9cb4c1615ae152515f3dcbe3bef603737d663839bf520
- b6ed38788fd409ada58fb0446d839eed07783e79b829e75ef031d67a53a3b62b
- b90a9ca23c1b2667d8a8a8e14bd3ccec4f928734e91dc28af26e69dafb991668
- f5bad2d671dc5b30fdbc93304e2d9b194033cc307099eae1d58cee17a2cb717a
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Win.Packed.Kovter-6895460-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\FC6A75BE78
- Value Name: b97dea2a
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
- Value Name: 99297e9b
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: cafa44a6
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: b612d32f
- C59C87A31F74FB56
- 1315B41013857E19
- 97[.]12[.]118[.]34
- 95[.]173[.]120[.]56
- 90[.]243[.]251[.]205
- 96[.]18[.]11[.]140
- N/A
- %LocalAppData%\recol\PqIpWoU.asARM
- %LocalAppData%\Temp\ay35fayo.2m3.ps1
- %LocalAppData%\Temp\uipfcjr2.khy.psm1
- 352bc4694ee225e59f50875fbfbe2502a0223daa22b94eafed6e997e71588433
- ae9789ced159c8fe284e49c8352a66070b8a52bc256847be11ad0890da6b1a99
- b93e29b1ed93143a85a7d6cff2cd87b5c12e8923bea9f50923dbae429c950f2f
- dbebf2bbd28c1bf5b327a09fef96cba4078ce033b52488ce936dd53e92302437
- dffa4d8bbde6b5efbc79a4a05df2e4528f5dc991783e81844685bdf1c175b716
- e1161786aaf5ce7cf3938e1a105a150f3e7e6c4ab44e1b6dc26004b07dbcc6cc
- e4d4dfa171983e794cf68492fcfd6bb7312b953d22ae03df64213a5dd6496ee3
- e79f05d135d2c8524a190bd7d22d20674a21c149cc379299011390b932e056af
- f7c9f1a37f688b54b3494696c2ac6898fb6945038f4306737299750bec901b20
- fa6adb0b0a129ada90e2dcef5dcd34c2cae28496689630e7f0415882f12e608a
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Malware.Upatre-6894504-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\FC6A75BE78
- Value Name: 0521341d
- <HKLM>\SOFTWARE\WOW6432NODE\6C5692EEDA48CF842254
- Value Name: 4DE9F1CC8F5AEB40A9
- N/A
- 139[.]59[.]81[.]114
- ncaappraisers[.]com
- %LocalAppData%\Temp\opera_autoupdater.exe
- %LocalAppData%\Temp\wadly.exe
- 15e6ce12614b3b296ddd76343b5703d87beb736b162128aedca6499e40ccdfed
- 1ad3cf284008b50456bdfd4b8b6bdb0558e5667c34d1406bd7f879b33e8cf6f5
- 24ebabc590cff41db4261eea662c91d3e3d48bc7da2be03009fddac26861117b
- 3ea2036f27be61f73ef313f78a094c767164becbcbbfc9c4c7a33f3160d9f2bf
- 498d367976283785672c2c695e29ad7b20a2b0157dc1dc13acef67426da96e58
- 4c9b775952a0b574d258a982b0fe3bfca25f450b7e4ddc76a20981432135afa3
- 5d9721eff25abcb7d7a4af4af2d0dd568b181375186ef20a024cb9408a1b3975
- 68c841e9b1e4d2b2cb65177913d0a7152decd5ecc15f9d424897f2b277ef75c8
- 7f26231615eab934cf6cf7d54c9ded34b04fc068fd9ee274b4037843ca22c69d
- 80e7912b1921cfb610b2b43d5ca74c3aa5c6c3edce4aac9bb554b58dc9ddd6e9
- 81c52a86cae959eac3382cb9b72a8afb47db16746b9e9c3b9254dc0353174530
- 886515171b4b044976140bcfe2036796c80320072f54ad60078203d7523aad1c
- 8a53bf2d3220ef740147699a1a801cc58e4b48052b9c5569f3659ba1a26e3a6f
- 8b241d4a533f3f6ac4819a22e7c1dd7f18556e1f6f835584973902e63ababb66
- 945055c780e4f5855616bab1b2b94807ae603c6b2c8cedfb0dd5f32a4c07a784
- a3438650289b8b3025f6d08414af69cafc016080868a0a30d48239716eea2420
- a95e1d9364069d02e6f844461cd9e7525f1c3f7a07960486403fee266f0fe8c1
- abb26593cd2fa77ee16fb0640465ec21592cda8d370c13a2fb74836e065b8f69
- c036fcf79a071d900b32100d015fc16bff5d82044139b6098eebc98009d2b056
- ca0bbd8f09581c6c0920c782a06d66e5cad25ce672f22e4ca0dde4ea98b905a6
- e45189ab53b35195f4676bc9081a605dc28cc79e26047763ccf2661d82120221
- ed75f96c614623b6c1aaa793cd8239c86049635d75406339ec778e7ba23eb317
- f9ccc2fe7e013cc9ee47eecc3dde93f6bae4aadc00a421254ed6fe35370b6984
- fcc0294acfcd7e2231d83841cb31e88363f75efab063c79c4a193f2c0cc26460
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Doc.Downloader.Emotet-6894115-0
Indicators of Compromise
Registry Keys
- N/A
- Global\I98B68E3C
- Global\M98B68E3C
- 181[.]197[.]2[.]252
- 94[.]73[.]147[.]237
- emseenerji[.]com
- %UserProfile%\208.exe
- %WinDir%\SysWOW64\SCwdrA.exe
- %LocalAppData%\Temp\CVR478.tmp
- %LocalAppData%\Temp\iidzocqo.viy.psm1
- %LocalAppData%\Temp\oflithzz.nz2.ps1
- 2ed65e9a1e796862f97eeebdf46152caf4f7f4204b801287bafe5b11e948ee1b
- 4c9295e6906108f3dc926a9591a148e4e2636a893d4d2505b35a0d030635462a
- 563991d43d484069890ca97745c1d7267c918afc260d31a52ec5bfc899a30c94
- 848b0b2455cb049ec8dfa798592de326b67abe036ae7a637c8aa3ab9e91f5cb7
- a06d630f62bc13cb49c794bf934a4a3dbe8cf63f352304e71c056199a065958f
- a42af575f713389ca1b0cd0156dceb753c1728cfe7c0e7a6036c53aef2d2d3fc
- b9f83bd5eebbdabf1cc5ff8587ca2f12a91f4905538e65587b35bd8bf1132e9c
- bf0ee1f25309aea8e27968f5d927fe8d05a66437cb86102d367305e61ec9f5d6
- c60eb3d68445ab0471aceef71bf75182d9d2f92e3ef3ab4fb148d8852dd2c5d0
- c9bdfb2d6ac9e493bc391b2f64b48d8d5cde10645ea921951b23112e6d73545c
- d818fd24d2ee5426ca535b7c966021cafbe7bcbb68b9d6ce420b9006859f2df0
- f3d7d9b36113ffc6aa4388f4d2f3f52349a3ba0984f9adc696b1a6d9db4108e0
- f832543e87f24eaa23f85c8976b79d7e49d1b4899f5358ba54a71b7c5f803e2d
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Malware
Win.Trojan.NetWire-6893426-1
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: internat.exe
- AlIgmljN
- 194[.]5[.]99[.]194
- N/A
- %AppData%\Install\Host.exe
- %UserProfile%\nltest\print.exe
- 1388ba005085c7a25e2680d0f7ee1d81c49924f3b555b4b6dbec68dddbf9b0e3
- 189525aa17b231ea223cd3c09443662341f908afc3973d88753ef78570b408ba
- 1cc74120569cff7c550b730223d0aed91a334c66f4dc2aa751e723e7c2ac2a14
- 1d9c379630d8d65bed03e26b9564651f0c16ae675ddcbf56ba607a107de27221
- 24f0f08e4774c2f4d1411ea8b57fcae3b37266830601f6ec30899126d93881f6
- 26917f6538fa6e8796c3c18c5f018370f6491adc63f4f466365d0c0186e9dd41
- 286a254ceeb034dc7417e5b9fab7141472a1db6500900f951775b07cd07f22c6
- 44cf94db97f1af9478f75e1df1afe36931fd741e1717601cc2e3d1d228c8b6c7
- 47571de1a9a22ae99d0cc5ac1d788a238dc1bdd416d32db63ffde7041bc98d1a
- 4eea828a9f2ff26440954da153a19d9667592a2c47206b7b5e161751794e3307
- 50b2adbbbba3fb086169174cd9c64a4f536c455231ae3dc93fb1ed6a71e48cad
- 530a89d43c4bd1ce99fd7dea8fa148158508653bd56063288da3e1086f274fe9
- 609676ce7da214d0340436956d1c4733a019811a6ffed5a74e5fa680ccfcdb0b
- 624b38be3943d4580a7bfe3d22a82dc451e9d5b4e8367886dda182e477e926d3
- 62b5df538e8e6a1737a0125202ca3a0d99610c08a839bb181cd6abaa9e768ceb
- 633c5f260bd8794b962c85de11f8eed31bb1bd14b5a11b9de564d6a06796ee7e
- 7220e58e3625c5d26b7be8450b1d8db9e10cdc4cca9173f372f2e7935fae18c3
- 7e366ff68193007a80f04d0cf6b33841dfc1a46b815992f241a51120cabab9ba
- 82a165f62e5c7727289e037c1dc4061aeb894403227a27b7366104ecd5cd08a9
- 8602358388e40b49cecbbc9e04e9863e95c7b24be53c053098b65553e252d74a
- 8f1ec1fa3db18ab4d7f716d55f67efb65e126742e7a0b3e276822d516bf53182
- 9b4f90c1ec5a35213b196fb4e0444f86a5ab394d0111a696ab197fbb5006cdb9
- a0aeb2aa7b2b833ff153bb372a6e3feadf04cf45035e49168331f26d9c887ec1
- a2327077fa20fc6c10e72031cb249a874531b376ad335bf5367f6a13566db109
- a513a5d7c1fcabdd53896d054eac221dcba70f4636b8d3c2f306f121ada943bf
Coverage
Screenshots of Detection
AMPThreatGrid