Microsoft has released its monthly set of security advisories for vulnerabilities that have been identified and addressed in various products. This month's advisory release addresses 81 new vulnerabilities with 27 of them rated critical, 52 rated important, and 2 rated moderate. These vulnerabilities impact Edge, Hyper-V, Internet Explorer, Office, Remote Desktop Protocol, Sharepoint, Windows Graphic Display Interface, Windows Kernel Mode Drivers, and more. In addition, Microsoft is also releasing an update for Adobe Flash Player embedded in Edge and Internet Explorer.
Note that the Bluetooth vulnerabilities known as "BlueBorne" that affected Windows have been patched in this latest release. For more information, please refer to CVE-2017-8628.
Vulnerabilities Rated Critical
The following vulnerabilities are rated "critical" by Microsoft:
The following briefly describes these vulnerabilities.
CVE-2017-8747, CVE-2017-8749 - Internet Explorer Memory Corruption Vulnerability
Two vulnerabilities have been identified in Internet Explorer that could result in remote code execution in the context of the current user. These vulnerabilities manifest due to improper handling of objects in memory when attempting to render a webpage. Both vulnerabilities could be exploited if, for example, a user visits a specially crafted webpage that exploits one of these flaws.
CVE-2017-8750 - Microsoft Browser Memory Corruption Vulnerability
A vulnerability have been identified in Edge and Internet Explorer that could result in remote code execution in the context of the current user. This vulnerability manifests due to improper handling of objects in memory when attempting to render a webpage. This vulnerability could be exploited if, for example, a user visits a specially crafted webpage that exploits this flaw.
Multiple CVEs - Microsoft Edge Memory Corruption Vulnerability
Multiple vulnerabilities have been identified in Microsoft Edge that could allow an attacker to execute arbitrary code on an affected host. These vulnerabilities manifest due to improper handling of objects in memory. Successful exploitation of this vulnerability would result in arbitrary code execution in the context of the current user. Users who visit a specially crafted web page under the control of the attacker could be exploited.
The following is a list of CVEs that reflect these vulnerabilities:
- CVE-2017-8731
- CVE-2017-8734
- CVE-2017-8751
- CVE-2017-8755
- CVE-2017-8756
- CVE-2017-11766
CVE-2017-8757 - Microsoft Edge Remote Code Execution Vulnerability
A vulnerability have been identified in Edge that could result in remote code execution in the context of the current user. This vulnerability manifests due to improper handling of objects in memory when attempting to render a webpage. This vulnerability could be exploited if, for example, a user visits a specially crafted webpage that exploits this flaw. Alternatively, an attacker could embed an ActiveX control marked "safe for initialization" within a Microsoft Office document that "hosts the browser rendering engine" and socially engineer the user to open the malicious document.
CVE-2017-8696 - Microsoft Graphics Component Remote Code Execution Vulnerability
A vulnerability has been identified in Windows Uniscribe that could allow an attacker to remotely execute arbitrary code on an affected host. This vulnerability manifests due to improper handling of objects in memory. Exploitation of this vulnerability could be achieved if a user navigates to a malicious web page or opens a malicious file designed to exploit this vulnerability. Successful exploitation would result in arbitrary code execution in the context of the current user.
CVE-2017-8728, CVE-2017-8737 - Microsoft PDF Remote Code Execution Vulnerability
Two vulnerabilities in the Microsoft Windows PDF library have been identified that could allow an attacker to execute arbitrary code on a targeted host. These vulnerabilities manifest due to improper handling of objects in memory. Successful exploitation of these vulnerabilities would result in arbitrary code execution in the context of the current user. Users who open a specially crafted PDF file or who visit a web page containing a specially crafted PDF could exploit these vulnerabilities.
CVE-2017-0161 - NetBIOS Remote Code Execution Vulnerability
A vulnerability in NetBT Session Services has been identified that could allow an attacker to execute arbitrary code on the targeted host remotely. This vulnerability manifests as a race condition "when NetBT fails to maintain certain sequencing requirements." An attacker who sends specially crafted NetBT Session Service packets to the targeted system could exploit this vulnerability and achieve remote code execution.
Multiple CVEs - Scripting Engine Memory Corruption Vulnerability
Multiple vulnerabilities have been identified in the Microsoft Browser JavaScript engine that could allow remote code execution to occur in the context of the current user. These vulnerabilities manifest due to improper handling of objects in memory, resulting in memory corruption. Exploitation of these vulnerabilities is achievable if a user visits a specially crafted web page that contains JavaScript designed to exploit one or more of these vulnerabilities.
The following is a list of CVEs that reflect these vulnerabilities:
- CVE-2017-8649
- CVE-2017-8660
- CVE-2017-8729
- CVE-2017-8738
- CVE-2017-8740
- CVE-2017-8741
- CVE-2017-8748
- CVE-2017-8752
- CVE-2017-8753
- CVE-2017-11764
CVE-2017-8682 - Win32k Graphics Remote Code Execution Vulnerability
A vulnerability in the Windows font library has been identified that could allow an attacker to execute arbitrary code on an affected host. This vulnerability manifests due to improper handling of embedded fonts. Successful exploitation of this vulnerability would result in arbitrary code execution in the context of the current user. For this vulnerability to be exploited, a user would need to either navigate to a specially crafted website or open a specially crafted document that is designed to exploit this flaw.
CVE-2017-8686 - Windows DHCP Server Remote Code Execution Vulnerability
A vulnerability has been identified in the Windows Server DHCP service where remote code execution could be achieved if exploited. This vulnerability manifests as a result of the service incorrectly handling DHCP packets. Successful exploitation could allow an attacker to remotely execute code on an affected host or create a denial of service condition. For this vulnerability to be exploited, an attacker would need to send a specially crafted packet to the DHCP server that is set to failover mode. If the server is not set to failover mode, the attack will not succeed.
CVE-2017-8676 - Windows GDI+ Information Disclosure Vulnerability
An information disclosure vulnerability have been identified in the Windows Graphics Device Interface+ (GDI+) that could allow an attacker to obtain potentially sensitive information about the affected host. This vulnerability manifests due to the Windows GDI+ component improperly handling objects in memory. An attacker who runs a specially crafted executable could exploit this vulnerability and leverage the information to further compromise the host.
Vulnerabilities Rated Important
The following vulnerabilities are rated "important" by Microsoft:
The following briefly describes these vulnerabilities.
CVE-2017-8759 - .NET Framework Remote Code Execution Vulnerability
A vulnerability has been identified in the Microsoft .NET Framework that could allow an attacker to execute arbitrary code on an affected device. This vulnerability manifests due to improperly handling untrusted input. Successful exploitation could result in an attacker being able to execute arbitrary code in the context of the current user. A user who opens a malicious document or application could be exploited and compromised via this vulnerability.
CVE-2017-9417 - Broadcom BCM43xx Remote Code Execution Vulnerability
A vulnerability has been identified in the Broadcom chipsets used in HoloLens that could allow an attacker to execute arbitrary code on an affected device. This vulnerability manifests due to improper handling of Wi-fi packets. Successful exploitation of this vulnerability could result in an attacker being able to take full control of the device with administrator privileges.
CVE-2017-8746 - Device Guard Security Feature Bypass Vulnerability
A vulnerability had been identified in Device Guard that could allow an attacker bypass a security control and inject malicious code into a Windows Powershell session. This vulnerability manifests as a flaw in how the Device Guard Code Integrity policy is implemented. An attacker who has access to a local machine could inject malicious into a script that is trusted by the Code Integrity policy. As a result, the injected code could run with the same trust level as the script, bypassing the Code Integrity policy control.
CVE-2017-8695 - Graphics Component Information Disclosure Vulnerability
An information disclosure vulnerability has been identified in Windows Uniscribe that could allow an attacker to obtain important system information. This information could then be used to further compromise a user's system via another vulnerability. Exploitation of this vulnerability could be achieved if a user opens a specially crafted document or visited a malicious web page that is designed to exploit this vulnerability.
CVE-2017-8704 - Hyper-V Denial of Service Vulnerability
A denial of service vulnerability has been identified in Microsoft Hyper-V that could cause the host machine to crash. This vulnerability manifests due to the host server improperly validating input from a privileged user within a guest operating system. An attacker who has privileged access in a guest operating system on the affected host could execute a specially crafted application could trigger this vulnerability.
Multiple CVEs - Hyper-V Information Disclosure Vulnerability
Multiple information disclosure vulnerabilities have been identified in Windows Hyper-V that could allow an attacker to access sensitive information on the Hyper-V host operating system. These vulnerabilities manifest due to Hyper-V improperly validating input from an authenticated user inside a guest operating system. An attacker who has access to a guest VM and executes a specially crafted application within the guest VM could exploit this vulnerability and obtain information on the Hyper-V host.
The following is a list of CVEs that reflect these vulnerabilities:
- CVE-2017-8706
- CVE-2017-8707
- CVE-2017-8711
- CVE-2017-8712
- CVE-2017-8713
CVE-2017-8733 - Internet Explorer Spoofing Vulnerability
A spoofing vulnerability in Internet Explorer has been identified that could allow an attacker to trick the user into believing they were visiting a legitimate web site. This vulnerability manifests due to Internet Explorer incorrectly handling specific HTML content. A user who navigates to a specially crafted web page under the control of the attacker could be exploited. As a result, this malicious website could then be used to serve spoofed content to the user or to serve as part of a exploit chain designed to compromise the affected host.
CVE-2017-8628 - Microsoft Bluetooth Driver Spoofing Vulnerability
A spoofing vulnerability has been identified in Microsoft's implementation of the Bluetooth stack and has been disclosed as part of "BlueBorne" series of vulnerabilities. This vulnerability could allow an attacker to perform a man-in-the-middle attack and force a user's device to "unknowingly route traffic through the attacker's computer." For this exploit to be possible, an attacker would need to be within physical proximity to the targeted device and the targeted device would need to have Bluetooth enabled. Note that if both of these conditions are satisfied, an attacker could "initiate a Bluetooth connection to the target computer without the user's knowledge."
CVE-2017-8736 - Microsoft Browser Information Disclosure Vulnerability
A vulnerability in Microsoft Edge and Internet Explorer has been identified that could allow an attacker to obtain information regarding the user's current session. This vulnerability manifests due to the browser improperly verifying parent domains in certain functionality. An attacker who socially engineers a user to visiting a specially crafted web page could exploit this flaw and obtain information that is specific to the parent domain.
CVE-2017-8597, CVE-2017-8648 - Microsoft Edge Information Disclosure Vulnerability
Multiple vulnerabilities in Microsoft Edge have been identified that could allow an attacker to discover sensitive information regarding the targeted system. These vulnerabilities manifest due to improper handling of objects in memory. Successful exploitation of these vulnerabilities could given an attacker the necessary information to further exploit additional vulnerabilities on the system.
CVE-2017-8643 - Microsoft Edge Information Disclosure Vulnerability
An vulnerability in Microsoft Edge has been identified that could permit the disclosure of potentially sensitive information. This vulnerability manifests due to Microsoft Edge improperly handling clipboard events. Exploitation of this vulnerability is achievable if an attacker socially engineers a user to open a specially crafted web page that exploits this flaw. As long has this web page remains open, an attacker would be able to able to gain knowledge of clipboard activities.
CVE-2017-8754 - Microsoft Edge Security Feature Bypass Vulnerability
A vulnerability in Microsoft Edge has been identified that could allow an attacker to bypass the Content Security Policy (CSP) feature. This vulnerability manifests due to improperly validating certain specially crafted documents. Successful exploitation could allow an attacker to redirect users to a malicious web page. Users who visit a specially crafted web page under the control of the attacker could be exploited. Alternatively, users who visit a compromised web page or who get served a malicious advertisement an attacker has injected into an advertising network could be exploited.
CVE-2017-8724 - Microsoft Edge Spoofing Vulnerability
A vulnerability in Edge has been identified that could allow an attacker to spoof content on a targeted host. This vulnerability manifests due to improper parsing of HTTP content. Successful exploitation of this vulnerability would result in the user being redirected to a web site of the attacker's choosing. This web site could then spoof content or serve as part of an exploit chain whereby the user could be exploited via another vulnerability. Scenarios where a user could be attacked include email or instant message vectors where the user clicks on a malicious link, or the user navigates to a specially crafted web page under the control of the attacker.
CVE-2017-8758 - Microsoft Exchange Cross-Site Scripting Vulnerability
A cross-site scripting vulnerability in Microsoft Exchange has been identified that could allow an attacker to perform a content/script injection attack. This vulnerability manifests due to Exchange failing to properly handle web requests. An attacker who sends an intended victim a specially crafted email containing a malicious link could exploit this vulnerability and potentially trick the user into disclosing sensitive information.
CVE-2017-11761 - Microsoft Exchange Information Disclosure Vulnerability
A vulnerability in Microsoft Exchange has been identified that could allow an attacker to obtain information regarding the affected server's local network. This vulnerability manifests as an information disclosure flaw due to improper input sanitization. An attacker who includes specially crafted tags in a Calendar-related message and sends this to an affected Exchange server could exploit this flaw and enumerate internal hosts assigned an RFC 1918 IP address. This information could then be used as part of a larger attack.
Multiple CVEs - Microsoft Office Memory Corruption Vulnerability
Multiple vulnerabilities have been identified affecting Microsoft Office that could allow an attacker to execute arbitrary code on an affected system. These vulnerabilities manifest due to Office improperly handling objects in memory. A users who opens a maliciously crafted Office document could be exploited, resulting in arbitrary code execution of the attacker's choice in the context of the current user. Scenarios where this could occur include email-based attacks, where the attacker sends the victim a message with a malicious attachment, or web-based attacks where the user downloads and opens a malicious Office document.
The following is a list of CVEs that reflect these vulnerabilities:
- CVE-2017-8630
- CVE-2017-8631
- CVE-2017-8632
- CVE-2017-8744
CVE-2017-8725 - Microsoft Office Publisher Remote Code Execution
A vulnerability has been identified affecting Microsoft Office Publisher that could allow an attacker to execute arbitrary code on an affected system. This vulnerability manifests due to Publisher improperly handling objects in memory. A users who opens a maliciously crafted Publisher document could be exploited, resulting in arbitrary code execution of the attacker's choice in the context of the current user. Scenarios where this could occur include email-based attacks, where the attacker sends the victim a message with a malicious attachment, or web-based attacks where the user downloads and opens a malicious Publisher document.
CVE-2017-8567 - Microsoft Office Remote Code Execution
A vulnerability has been identified affecting Microsoft Office that could allow an attacker to execute arbitrary code on an affected system. This vulnerability manifests due to Office improperly handling objects in memory. A user who opens a maliciously crafted document could be exploited, resulting in arbitrary code execution of the attacker's choice in the context of the current user. Scenarios where this could occur include email-based attacks, where the attacker sends the victim a message with a malicious attachment, or web-based attacks where the user downloads and opens a malicious Office document. Note that Preview Pane is not an attack vector for this vulnerability.
CVE-2017-8745, CVE-2017-8629 - Microsoft SharePoint XSS Vulnerability
Two vulnerabilities in Microsoft Sharepoint have been identified that could could allow an attacker to execute a cross-site scripting (XSS) attack. These vulnerabilities manifest due to Sharepoint Server improperly sanitizing specific web requests from a user. Successful exploitation of these flaws could allow an attacker to execute script in the context of the current user, read content that the attacker would not have permission to otherwise view, or execute actions on behalf of the affected user.
CVE-2017-8742, CVE-2017-8743 - PowerPoint Remote Code Execution Vulnerability
Two vulnerabilities have been identified affecting Microsoft Office Powerpoint that could allow an attacker to execute arbitrary code on an affected system. These vulnerabilities manifest due to Powerpoint improperly handling objects in memory. A user who opens a maliciously crafted Powerpoint document could be exploited, resulting in arbitrary code execution of the attacker's choice in the context of the current user. Scenarios where this could occur include email-based attacks, where the attacker sends the victim a message with a malicious attachment, or web-based attacks where the user downloads and opens a malicious Powerpoint document.
CVE-2017-8714 - Remote Desktop Virtual Host Remote Code Execution Vulnerability
A vulnerability has been identified in the VM Host Agent Service of Remote Desktop Virtual Host that could allow an attacker to execute arbitrary code on an affected host. This vulnerability manifests due to improperly validating input from an authenticated user within a guest operating system. Exploitation of this flaw is achievable if an attacker issues a "specially crafted certificate" within a guest operating system, causing the "VM host agent service on the host operating system to execute arbitrary code." Microsoft notes that the Remote Desktop Virtual Host role is not enabled by default.
CVE-2017-8739 - Scripting Engine Information Disclosure Vulnerability
A vulnerability in Microsoft Edge has been identified that could disclose sensitive information to an attacker. This vulnerability manifests due to improper handling of objects in memory. Successful exploitation of this vulnerability would result in an attacker obtaining information that could then be used to further exploit the system. Users who visit a specially crafted web page under the control of the attacker could be exploited.
CVE-2017-8692 - Uniscribe Remote Code Execution Vulnerability
An arbitrary code execution vulnerability has been identified in Windows Uniscribe that could allow an attacker to execute code in the context of the current user. This vulnerability manifests due to Uniscribe improperly handling objects in memory. Exploitation of this vulnerability could be achieved if a user navigates to a malicious web page or opens a malicious file designed to exploit this vulnerability.
CVE-2017-8593 - Win32k Elevation of Privilege Vulnerability
A vulnerability in Windows Kernel Mode Drivers has been identified that could allow a privilege escalation attack to occur. This vulnerability manifests due to improper handling of objects in memory. Successful exploitation of this vulnerability could result in an attacker being able to execute arbitrary code in kernel mode. An attacker who executes a specially crafted executable could exploit this vulnerability and as a result, gain full control of the affected system.
CVE-2017-8720 - Win32k Elevation of Privilege Vulnerability
A vulnerability in the Win32k component in Windows has been identified that could allow a privilege escalation attack to occur. This vulnerability manifests due to improper handling of objects in memory. Successful exploitation of this vulnerability would result in an attacker obtaining administrator privileges on the targeted system. Users who run a specially crafted executable that exploits this vulnerability could leverage this vulnerability to perform actions as an administrator on the affected system.
CVE-2017-8683 - Win32k Graphics Information Disclosure Vulnerability
An information disclosure vulnerability has been identified in the Windows Graphics Component that could allow an attacker to gain information about the host. This vulnerability manifests due to the Graphics Component improperly handling objects in memory. An attacker who runs a specially crafted executable could exploit this vulnerability and leverage the information to further compromise the host.
CVE-2017-8678 - Win32k Information Disclosure Vulnerability
An information disclosure vulnerability has been identified in the Windows kernel that could allow an attacker to gain information about the host. This vulnerability manifests due to the kernel improperly handling objects in memory. An attacker who runs a specially crafted executable could exploit this vulnerability and leverage the information to further compromise the host.
Multiple CVEs - Win32k Information Disclosure Vulnerability
Multiple information disclosure vulnerabilities have been identified in the Windows Graphics Device Interface+ (GDI+) component that could allow an attacker to gain information about the host. This vulnerability manifests due to the GDI+ component improperly handling objects in memory. An attacker who runs a specially crafted executable could exploit this vulnerability and leverage the information to further compromise the host.
The following is a list of CVEs that reflect these vulnerabilities:
- CVE-2017-8677
- CVE-2017-8680
- CVE-2017-8681
CVE-2017-8687 - Win32k Information Disclosure Vulnerability
An information disclosure vulnerability has been identified in the Windows kernel that could allow an attacker to gain information which could lead to a Kernel Address Space Layout Randomization (KASLR) bypass. This vulnerability manifests due to the kernel improperly handling objects in memory. An attacker who runs a specially crafted executable could exploit this vulnerability and obtain the "memory address of a kernel object," allowing an attacker to leverage the information to further compromise the host.
CVE-2017-8702 - Windows Elevation of Privilege Vulnerability
A vulnerability in the Windows Error Reporting (WER) has been identified that could allow a privilege escalation attack to occur. Successful exploitation of this vulnerability would result in an attacker obtaining administrator privileges on the targeted system.
Multiple CVEs - Windows GDI+ Information Disclosure Vulnerability
Multiple information disclosure vulnerabilities have been identified in the Windows Graphics Device Interface+ (GDI+) that could allow an attacker to obtain potentially sensitive information about the affected host. These vulnerabilities manifest due to the Windows GDI+ component improperly handling objects in memory. An attacker who runs a specially crafted executable could exploit this vulnerability and leverage the information to further compromise the host.
The following is a list of CVEs that reflect these vulnerabilities:
- CVE-2017-8684
- CVE-2017-8685
- CVE-2017-8688
CVE-2017-8710 - Windows Information Disclosure Vulnerability
An information disclosure vulnerability in the Windows System Information Console has been identified that could allow an attacker to read arbitrary files on an affected system. This vulnerability manifests due to improper parsing of XML input which contains a reference to an external entity. An attacker who creates specially crafted file containing XML content and either opens the file or socially engineers an user to open the file on an affected system could exploit this vulnerability.
Multiple CVEs - Windows Kernel Information Disclosure Vulnerability
Multiple information disclosure vulnerabilities have been identified in the Windows kernel that could allow an attacker gain information about the host. These vulnerabilities manifest due to the kernel improperly handling objects in memory. An attacker who runs a specially crafted executable could exploit these vulnerabilities and leverage the information to further compromise the host.
The following is a list of CVEs that reflect these vulnerabilities:
- CVE-2017-8679
- CVE-2017-8709
- CVE-2017-8719
CVE-2017-8708 - Windows Kernel Information Disclosure Vulnerability
An information disclosure vulnerability has been identified in the Windows kernel that could allow an attacker to gain information which could lead to a Kernel Address Space Layout Randomization (KASLR) bypass. This vulnerability manifests due to the kernel failing to properly initialize a memory address. An attacker who runs a specially crafted executable could exploit this vulnerability and obtain the "base address of the kernel driver from a compromised process," allowing an attacker to leverage the information to further compromise the host.
CVE-2017-8716 - Windows Security Feature Bypass Vulnerability
A vulnerability has been identified in Windows Control Flow Guard that could allow an attacker bypass its intended function. This vulnerability manifests due to the Control Flow Guard mishandling objects in memory. An attacker who runs a specially crafted executable on an affected host could exploit this vulnerability.
CVE-2017-8699 - Windows Shell Remote Code Execution Vulnerability
An arbitrary code execution vulnerability has been identified in the Windows Shell that could allow an attacker to execute code in the context of the current user. This vulnerability manifests as a result of Window Shell improperly validating file copy destinations. An attacker who opens a specially crafted file could exploit this vulnerability. Scenarios where end-user could be compromised include email-based attacks, where an attacker send the victim a malicious attachment that the user opens, or a web-based attack where the user downloads and opens a malicious file.
Vulnerabilities Rated Moderate
The following vulnerabilities are rated "moderate" by Microsoft:
- CVE-2017-8723 - Microsoft Edge Security Feature Bypass Vulnerability
- CVE-2017-8735 - Internet Explorer Memory Corruption Vulnerability
The following briefly describes these vulnerabilities.
CVE-2017-8723 - Microsoft Edge Security Feature Bypass Vulnerability
A vulnerability in Microsoft Edge has been identified that could allow an attacker to bypass the Content Security Policy (CSP) feature. This vulnerability manifests due to improperly validating certain specially crafted documents. Successful exploitation could allow an attacker to redirect users to a malicious web page. Users who visit a specially crafted web page under the control of the attacker could be exploited. Alternatively, users who visit a compromised web page or who get served a malicious advertisement an attacker has injected into an advertising network could be exploited.
CVE-2017-8735 - Microsoft Edge Spoofing Vulnerability
A vulnerability in Edge has been identified that could allow an attacker to spoof content on a targeted host. This vulnerability manifests due to improper parsing of HTTP content. Successful exploitation of this vulnerability would result in the user being redirected to a web site of the attacker's choosing. This web site could then spoof content or serve as part of an exploit chain whereby the user could be exploited via another vulnerability. Scenarios where a user could be attacked include email or instant message vectors where the user clicks on a malicious link, or if the user navigates to a specially crafted web page under the control of the attacker.
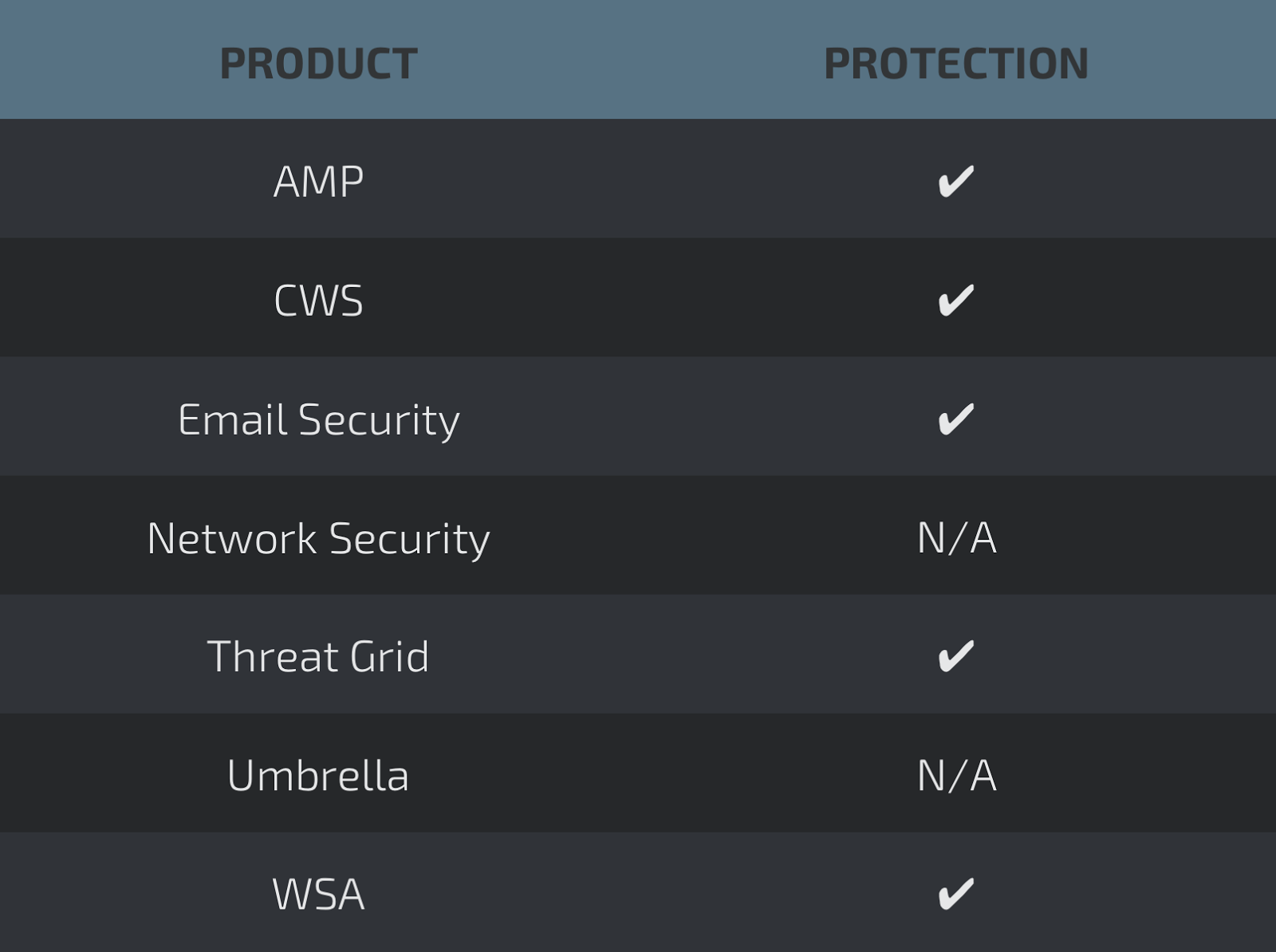
Coverage
In response to these vulnerability disclosures, Talos is releasing the following rules to address these vulnerabilities. Please note that additional rules may be released at a future date and current rules are subject to change pending additional vulnerability information. Firepower customers should use the latest update to their ruleset by updating their SRU. Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on
Snort.org.
Snort Rules:- 42285-42286
- 42311-42312
- 42749-42750
- 44331-44336
- 44338-44343
- 44349-44350
- 44353-44357
![]()
![]()